 These principles have been around far longer than COVID-19, but they’re now more important than ever. Below, we discuss each principle and the associated practices that help keep your business compliant and secure.
These principles have been around far longer than COVID-19, but they’re now more important than ever. Below, we discuss each principle and the associated practices that help keep your business compliant and secure.
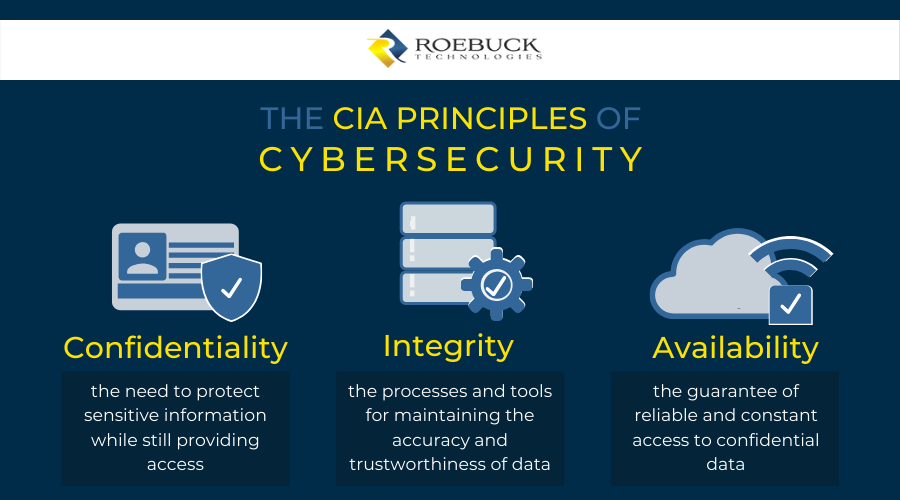
COVID-19 cybersecurity framework: Confidentiality, Integrity, Availability

With Florida businesses topping the list as the second most likely at risk of cybercrime (just after California) and more employees working remotely in the wake of COVID-19, cybersecurity has become a high-priority investment.
Considering the wide range of practices, tools, and services available, how does one determine a quality security system?
The CIA principles of security — a model designed to help business owners form their policies around information security — provides useful guidance. Standing for confidentiality, integrity, and availability, the CIA framework ensures your data remains protected, accurate, and exclusively accessible to authorized members.
 These principles have been around far longer than COVID-19, but they’re now more important than ever. Below, we discuss each principle and the associated practices that help keep your business compliant and secure.
It’s also important to ensure everyone has adequate bandwidth and eliminate any bottlenecks and “bandwidth hogs.” Low bandwidth and spikes of unnecessarily high usage can slow down communications and performance across your network, causing problems in data availability and efficient access.
Last but not least, a proper disaster recovery plan is vital. The risks of data loss, theft, or interruptions are higher than ever as employees work from personal devices and hackers create new attacks that prey on coronavirus fears. Ideally, data backups should be stored in the cloud as well as on hard drives in a fireproof, waterproof, isolated location.
No matter how small or large a business is, an effective, robust cybersecurity system is necessary.
Roebuck Technologies offers companies end-to-end security solutions to keep their data safe from both common and advanced digital threats. Our experts employ a stringent combination of products and services to help you form strong, reliable defense systems for your business. Enquire with us today to ensure the confidentiality, integrity, and availability of your data.
These principles have been around far longer than COVID-19, but they’re now more important than ever. Below, we discuss each principle and the associated practices that help keep your business compliant and secure.
It’s also important to ensure everyone has adequate bandwidth and eliminate any bottlenecks and “bandwidth hogs.” Low bandwidth and spikes of unnecessarily high usage can slow down communications and performance across your network, causing problems in data availability and efficient access.
Last but not least, a proper disaster recovery plan is vital. The risks of data loss, theft, or interruptions are higher than ever as employees work from personal devices and hackers create new attacks that prey on coronavirus fears. Ideally, data backups should be stored in the cloud as well as on hard drives in a fireproof, waterproof, isolated location.
No matter how small or large a business is, an effective, robust cybersecurity system is necessary.
Roebuck Technologies offers companies end-to-end security solutions to keep their data safe from both common and advanced digital threats. Our experts employ a stringent combination of products and services to help you form strong, reliable defense systems for your business. Enquire with us today to ensure the confidentiality, integrity, and availability of your data.
 These principles have been around far longer than COVID-19, but they’re now more important than ever. Below, we discuss each principle and the associated practices that help keep your business compliant and secure.
These principles have been around far longer than COVID-19, but they’re now more important than ever. Below, we discuss each principle and the associated practices that help keep your business compliant and secure.
