With Florida businesses topping the list as the second most likely at risk of cybercrime (just after California) and more employees working remotely in the wake of COVID-19, cybersecurity has become a high-priority investment.
Considering the wide range of practices, tools, and services available, how does one determine a quality security system?
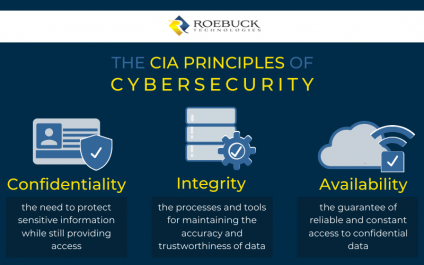
The CIA principles of security — a model designed to help business owners form their policies around information security — provides useful guidance.